
ParaSwap DAO members were split, with some supporting the conditional return of the fees and others voting against the refund.
Dig Deeper, Invest Smarter

ParaSwap DAO members were split, with some supporting the conditional return of the fees and others voting against the refund.

Japanese Bitcoin spot ETF may not arrive as early as once expected this week.
SBI Holdings denied earlier reports that it has formally filed for crypto-related exchange-traded funds (ETFs) in Japan, clarifying that the plans remain in the development phase.
“Contrary to some media reports, we have not filed any applications with the authority to form an ETF related to crypto assets,” the SBI spokesperson told Cointelegraph on Friday. “It is only at the planning stage.”
The spokesperson said SBI will not submit any ETF applications until Japan’s Financial Services Agency (FSA) finalizes its approach to classifying crypto assets.
“In Japan, ETFs that incorporate crypto assets are expected to be approved in a way that aligns with the responses of the financial authorities and tax authorities,” the SBI representative said. “Therefore, the filing will be done after these legal revisions have been made.”
In its Q2 results announcement a week ago, SBI introduced the plan for two new ETFs: a hybrid product combining gold and digital assets, and another holding spot Bitcoin and XRP. The reports pointed to language in the company’s latest earnings presentation as evidence.
However, the presentation material did not explicitly confirm any regulatory filings, and SBI has moved to set the record straight.
In June, FSA proposed recognizing certain digital assets as financial products under the Financial Instruments and Exchange Act (FIEA), the framework that governs traditional securities.
If approved, the change could enable the first publicly listed crypto ETFs in Japan. While clarifying it has yet to file applications, SBI has already taken steps to position itself for Japan’s anticipated ETF market. As BeInCrypto previously reported, the company has partnered with US investment firm Franklin Templeton to create a new digital asset management joint venture in Japan.
Nikkei reported that SBI will hold a 51% majority stake in the new firm, while Franklin Templeton will own the remaining shares. The partnership is designed to launch Bitcoin ETFs as soon as the FSA grants approval. The joint venture also intends to leverage Franklin Templeton’s expertise in asset tokenization to expand future product offerings.
This move runs parallel to SBI’s plans for two ETF concepts under its subsidiary SBI Global Asset Management: a pure-play spot ETF for Bitcoin and XRP, and a hybrid fund with at least 51% allocated to gold and the remainder to digital assets. The company aims to offer these products to individual investors first, aligning with its mission to “promote the democratization of alternative investments.”
SBI’s inclusion of XRP reflects its longstanding relationship with Ripple, where it remains a major shareholder. The firm has actively promoted XRP in cross-border payments throughout Asia. Analysts say a regulated ETF with direct XRP exposure could help legitimize the token for institutional adoption in Japan.
The hybrid gold-crypto ETF concept is aimed at appealing to both digital asset enthusiasts and risk-averse investors, merging the growth potential of crypto with the perceived stability of gold.
SBI’s ETF ambitions are part of a broader Web3 strategy. The firm is expanding stablecoin initiatives, including USDC, Ripple’s RLUSD, and a planned yen-denominated stablecoin, to integrate securities, banking, and digital assets into a single financial infrastructure.
Industry observers see these steps as positioning ahead of a likely market shift once ETF approval arrives. The introduction of regulated crypto ETFs could unlock new institutional capital, especially from pension funds and asset managers who have avoided direct crypto exposure due to regulatory and tax hurdles.
While optimism is building—especially within the XRP community—industry experts warn that regulatory review and product vetting will take time. SBI has reiterated that all publicly available information on its ETF plans is contained within its earnings presentation and related statements, with no further details released on fees, custody, or launch dates.
If Japan’s FSA finalizes the proposed legal revisions, the country could join the United States and Canada in offering spot crypto ETFs. For SBI, early entry could cement its leadership in Japan’s evolving financial landscape, while partnerships like the Franklin Templeton venture underscore its intent to be ready the moment regulators open the door.
The post Japan Crypto ETF Not Officially Filed, Plans Still in Development Phase appeared first on BeInCrypto.

Coinbase announced that it is delisting MOVE, which subsequently plunged over 16%. The exchange did not describe any specific reasoning for this action, leading community speculation to flourish.
New evidence alleges that Movement Labs was directly or indirectly involved in a market maker dumping 66 million MOVE tokens. Coinbase may have lost confidence in the project between those rumors and a delayed airdrop.
Although Coinbase has the well-documented ability to boost certain cryptoassets by listing them, the reverse is apparently also true. The exchange will suspend all MOVE trading in exactly two weeks, immediately causing the asset to plummet.
In addition to this 16% price drop, MOVE’s daily trading volume surged 130%. This suggests that MOVE holders are selling their assets after Coinbase’s delisting announcement.
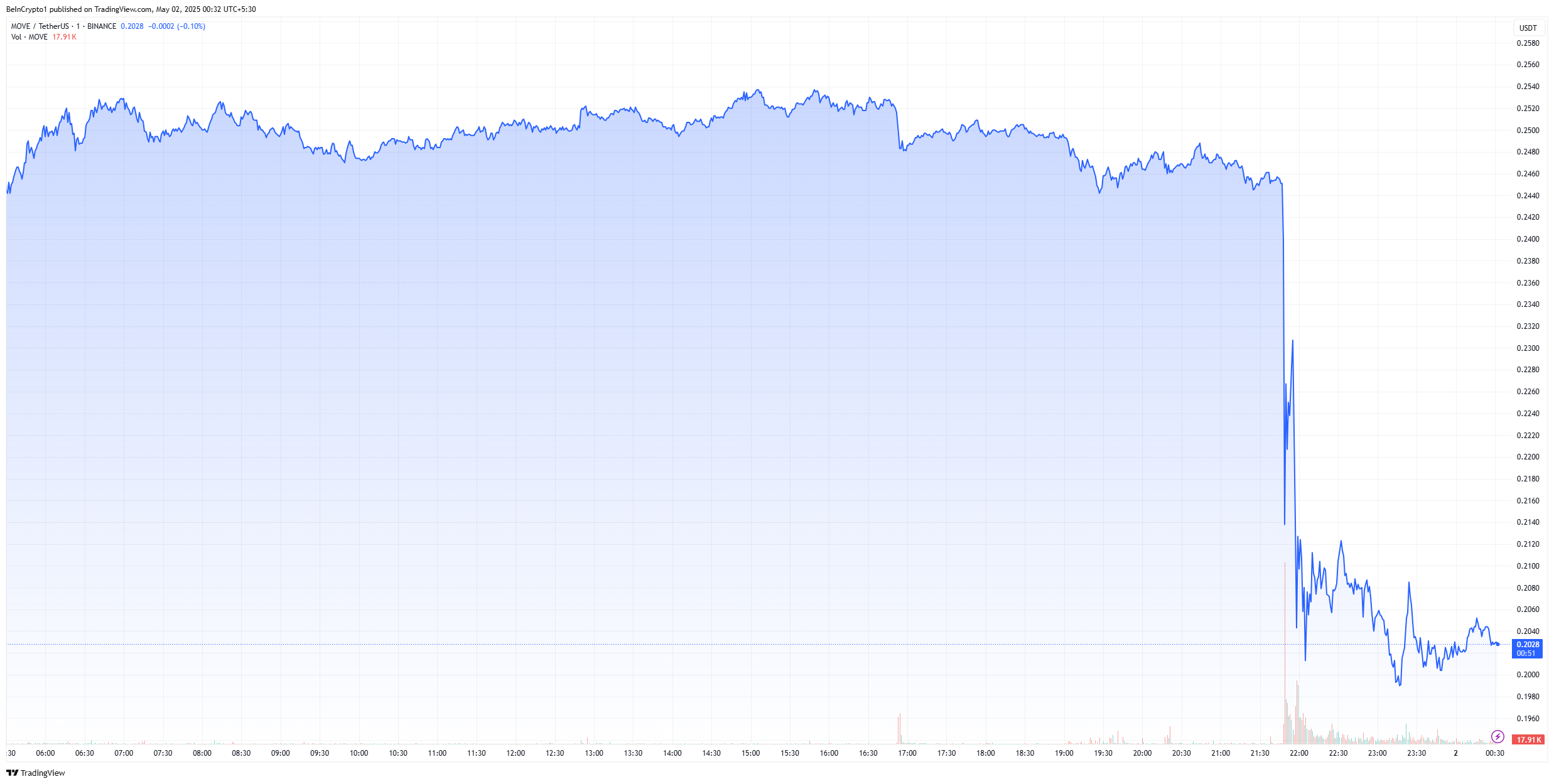
This is a serious blow to Movement Network’s credibility and reputation. The project showed significant potential and even outperformed Bitcoin and Ethereum during the Q1 2025 cycle. It also raised $100 million in VC funding earlier this year, backed by notable investors.
However, Coinbase’s delisting is not unfounded. Earlier today, Movement Labs announced that a planned airdrop was being delayed, helping spark frustration. That may have been the final straw for Coinbase, on top of pre-existing problems.
From a perspective of someone who’s been building on Movement since day one — before mainnet, before the hype, before the community we have today even existed:
The recent MM incident and MoveDrop delay are real setbacks. There’s no sugarcoating it. But surely they don’t define… https://t.co/rfSrUKxxpq pic.twitter.com/STng5Oid4P
— Mosaic (@mosaicagg) May 1, 2025
Specifically, Movement Labs claimed it would investigate an instance of potential fraud in mid-March. A market maker dumped 66 million MOVE tokens, triggering a sharp price drop.
New evidence has come to light, leading users to allege that Movement Labs was directly or indirectly complicit in these dealings. The company allegedly loaned 50% of MOVE’s supply to investment platform Web3Port, which proceeded to dump a large volume of tokens.
Based on these incidents, the community fears a repeat of MANTRA’s historic OM crash. Meanwhile, Movement Labs is backed by the Trump Family’s World Liberty Financial. The DeFi project holds more than 7 million MOVE tokens.
The post MOVE Crashes 16% After Coinbase Delisting – Here’s What Happened appeared first on BeInCrypto.

As technology continues to evolve and users seek more immersive entertainment experiences, the GameFi market is seeing exponential growth and is expected to attract a wave of investors and players in the coming years. Amidst this momentum, Puffverse has emerged as a dazzling new force in the GameFi space, thanks to its innovative 3D virtual world concept and strong backing.
Puffverse is more than just a gaming platform. It’s an ambitious bridge aiming to seamlessly connect the Web3 virtual world with the Web2 real world, offering users a Disney-like 3D metaverse filled with endless possibilities.
The development team behind Puffverse is composed of top-tier talent from industry giants such as Alibaba and former Xiaomi teams, with deep technical expertise and rich experience. The project has also earned the support of leading investment institutions including Animoca, Foresight Ventures, Spartan, and HashKey, laying a solid foundation for Puffverse’s steady growth and positioning it as a standout in the GameFi track.
Now launching on Gate.io Launchpad, Puffverse offers participants a valuable opportunity to get early exposure and potentially benefit from its future growth. This article provides a comprehensive analysis of Puffverse’s project highlights, core team, tokenomics, and investment potential—unveiling the mystery behind this promising project.
Crafted by the software team formerly behind Xiaomi Games, Puffverse is a GameFi project centered around a 3D virtual world. Unlike traditional single-character systems, Puffverse emphasizes the question “Who am I?” by offering a range of characters for players to choose from.
Project Overview
Summary: Puffverse is a 3D metaverse fantasy world reminiscent of Disney. It aims to bridge the virtual world of Web3 with the real world of Web2, offering more than just party games or a cloud gaming platform.
Puffverse’s native token, PFVS, is the core of its entire ecosystem. Below is the key information about the token:
As the very first Gate.io Launchpad project, Puffverse (PFVS), is about to launch its commitment round. Users can commit USDT to receive PFVS tokens. Details are as follows:
Subscription Basic Information
Web: Log in to your Gate.io account and complete identity verification → Click “Launch” and select “Launchpad” → Choose the project you want to participate in and click “Commit Now” → Enter the commitment amount and confirm.
APP: Please upgrade to version 6.58.5 or above, log in to your Gate.io account, and complete identity verification → Tap “Earn” and select “Launchpad” → Choose the project you want to participate in and tap “Commit Now” → Enter the commitment amount and confirm.
Team Overview
The Puffverse team is composed of elite professionals from renowned tech companies such as Alibaba and Xiaomi. With solid technical capabilities and extensive industry experience in game development and operations, the team provides robust support for Puffverse’s ongoing innovation and development. Their keen industry insights enable the project to stand out in a competitive market.
Technical Infrastructure
Puffverse is built on advanced blockchain and 3D virtual reality technologies. Its smart contract architecture and decentralized governance system offer users an immersive virtual experience. The project also utilizes state-of-the-art game engines and optimization techniques to ensure smooth gameplay within the metaverse.
Top-Tier Investment Network
Puffverse boasts an impressive roster of investors, including Animoca, Arcane, Foresight Ventures, Spartan, HashKey, and Sky Mavis. These institutions not only provide financial support but also bring strategic resources and industry expertise, accelerating Puffverse’s rise in the GameFi space.
Investment Value
Puffverse’s investment potential lies in its unique 3D virtual world design and the strength of its technical team. With an innovative tokenomics model and a sustainable governance mechanism, Puffverse effectively motivates community participation and development, making it a project with long-term growth potential in the GameFi industry.
Unique Economic Model
At the heart of Puffverse is the PFVS token, designed to drive ecosystem operations. Beyond serving as a transactional medium and incentive tool, PFVS plays a vital role in ecosystem expansion and governance. Its well-balanced distribution and unlock model support long-term ecosystem sustainability and user engagement.
At the same time, PuffGo does not overlook the Web2 market. The game allows both web2 and web3 players to participate freely and blend in seamlessly. Web2 players can enjoy the game through traditional in-app purchases, filling a market gap in mobile party games. While web3 players can join the league and utilize their NFTs and tokens to engage in skill-to-earn model, enabling gameplay while generating earnings.
Efficient Governance System
Puffverse features a decentralized governance framework powered by smart contracts and community voting. This ensures transparency and efficiency in decision-making, fostering greater user trust and participation.
Puffverse has already made a notable impact in the fusion of GameFi and the 3D metaverse, backed by a top-tier team, strong investors, and a forward-thinking token economy. As the TGE approaches in May 2025, the project is set to enter an exciting new phase, bringing users an immersive experience unlike any other.
Gate.io Launchpad offers Puffverse a global stage, inviting users to engage with this innovative project early. For those focused on GameFi and metaverse development, Puffverse is undoubtedly a project worth watching. Seize this opportunity and join Puffverse in opening a new chapter in 3D metaverse gaming, where imagination meets the future of digital entertainment.
Disclaimer: The content herein does not constitute any offer, solicitation, or recommendation. You should always seek independent professional advice before making any investment decisions. Please be noted that Gate.io may restrict or prohibit the use of all or a portion of the Services from Restricted Locations. For more information, please read the User Agreement.
The post Puffverse Launches on Gate.io Launchpad: Unlocking Infinite Possibilities in the GameFi 3D Metaverse appeared first on BeInCrypto.
